SE
Syllabus
Text Books/ Weblinks/Material
Mostly Repeated Previous Paper Questions for Class Test
Previous Papers
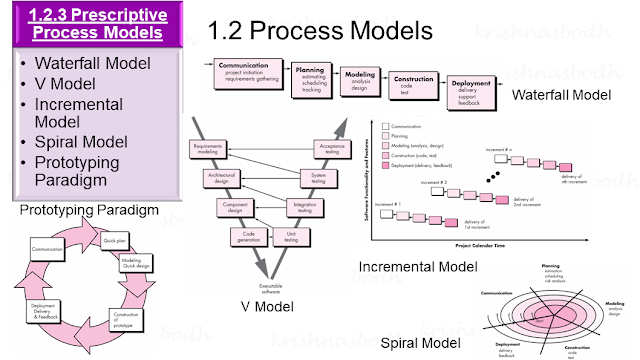
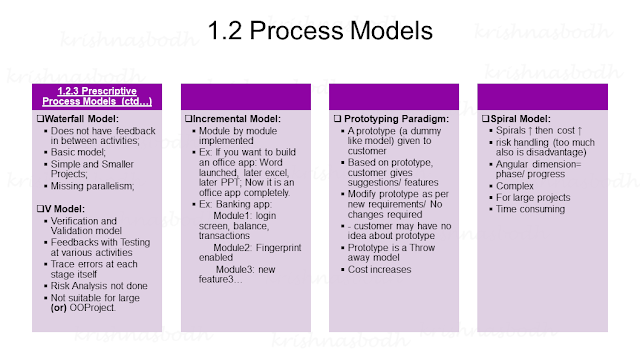
Unit-1: Software and Software Engineering; Process Models;
Assignment Unit-1
- Discuss the nature of software. K2
- Explain in Detail about Evolutionary process model. K2
- Explain the importance of Unified process. K2
- Outline the Umbrella activities needed for a software process. K2
- Analyze all the software Myths and realities. K4
- Explain in Detail about Incremental process model. K2
- Discuss about the Unique Nature of Webapps. K2
- Explain regarding Personal and team process models. K2
- Explain waterfall model for software development. K2
Quiz Unit-1
1. With respect to time and compared to ideal case, Software (actual) failure rate _____________.
(A) increases due to side effects (B) decreases (C) contant (D) zero
2. WebApps present information based on _________.
(A) text (B) limited graphics (C) both (A) and (B) (D) they don't exist
3. Legacy software is _________.
(A) latest (B) branded (C) both (A) and (B) (D) oldest (E) both (B) and (D)
4. Software Engineering layers (from top to bottom) are _________.
Tools =1, quality focus=2, process=3, methods=4
(A) 3,1,4,2 (B) 4,1,2,3 (C) 2,4,1,3 (D) 1,4,3,2
5. The given statement is:____________
Statement: If I decide to outsource the software project to a third party, I can just relax and let that firm build it.
Myth =1, Reality=2, Customer=3, Management=4, Practitioner=5
(A)1,3 (B) 1, 5 (C) 1, 4 (D) 2, 4 (E)2, 5 (F)2, 3
6. Incremental process models are _________ in nature and produce working versions of software quite rapidly.
(A) non-cooperative (B) iterative (C) inactive (D) insensitive
KEY: 1-A, 2-C, 3-E, 4-D, 5-B, 6-B
Unit-2: Agility, Principles that Guide Practice, Understanding Requirements
Assignment Unit-2
- What is the purpose of Agile Process Model? Discuss about Extreme Programming?
- Illustrate the different Elements of Analysis model?
- Clearly Discuss about The Principles That Guide Each Framework Activity
- Discuss about Software Engineering Knowledge and Core Principles?
- Explain about Requirement Elicitation.
- Discuss briefly about Establishing the Groundwork
- Demonstrate about different Agile Process Models.
- Distinguish between negotiating and validating Requirements?
- Give a Brief note on Building the Requirements Model
Quiz Unit-2
1. Ability to adpt to the changes _____________.
(A) Agility (B) process (C) task (D) activity
2.As time progresses, Development cost for conventional software processes is ________ than an agile process.
(A) lesser (B) zero (C) higher (D) unpredictable
3. Agile software process must adapt __________.
(A) not needed (B) decremented (C) derivated (D) incrementally
4. In order to achieve effective communication between software engineers and other stakeholders. ________ emphasizes close, yet informal (verbal) collaboration between customers and developers
(A) conventional process (B) legacy (C) formal(Word,PPT) (D) informal(Verbal)
5. Feedback is derived from three sources: the implemented software itself, the customer, and other ____________ members
(A) drivers (B) software team (C) third party D) unnecessary stakeholders.
6. XP Process starts with listening requirements that create _____________
(A) project itslef (B) stories (C) process framework (D) coding
KEY: 1-A, 2-C, 3-D, 4-D, 5-B, 6-B
Lecture Notes: Unit-3: Requirements Modeling { (Scenarios, Information, Analysis Classes), (Flow, Behavior Patterns, WebApps)}
Assignment Unit-3
- Explain in detail Requirements Analysis.
- Give a brief note on Class-Responsibility-Collaborator (CRC) Modeling
- Explain in detail Patterns for Requirements Modelling
- Discuss in detail Data Modeling Concepts.
- Explain in detail Requirements Modeling for WebApps.
- Explain about Creating a Behavioral Model
- Explain in detail Requirements Modeling Strategies
- Demonstrate about Flow-Oriented Modeling
- Discuss in detail about UML Models That Supplement the Use Case
Quiz Unit-3
1. ________-based models of requirements from the point of view of various system “actors
(A) Scenario (B) process (C) task (D) activity
2. ______-oriented models that represent the functional elements of the system and how they transform data as it moves through the system
(A) Model (B) Process (C) Flow (D) Design
3. ________ models that depict how the software behaves as a consequence of external “events”
(A) Flow (B) Behavioral (C) Scenario (D) Activity
4. UML = __________
(A) Unidentified Modeling Language (B) Unique Modeling Language (C) Unified Markup Language (D) Unified Modeling Language
5. A ________ is a representation of composite information that must be understood by software
(A) sentence (B) data object (C) plan (D) process
6. ________ describe a class that has been selected for inclusion in the requirements model.
(A) Process (B) Attributes (C) Task (D) Activity
7. CRC = _______ _________ ______
(A) Class-Responsibility-Collaborator (B) Concept-Responsibility-Collaborator (C) Class-Request-Collaborator (D) Clas-Responsibility-Clearance
8. DFD
(A) disk flow diagram (B) data flaw diagram (C) data flow diagram (D) disk flaw diagram
9. PSPEC
(A) plan specification (B) process specification (C) process speculation (D) plan speculation
10. The _______model indicates how software will respond to external events or stimuli.
(A) behavioral (B) unity (C) blackbox (D) task
11. A _________ state is simply the current status of all of an object’s attributes
(A) complex (B) simple (C) active (D) passive
12. An _______ occurs concurrently with the state transition or as a consequence of it and generally involves one or more operations (responsibilities) of the object
(A) assessment (B) activity (C) action (D) assurance
13. ______________ in UML, indicates how events cause transitions from object to object
(A) simple diagram (B) sequence diagram (C) process diagram (D) selection diagram
14. A ___________is a pattern that describes a small set of coherent use cases that together describe a basic generic application
(A) semantic analysis pattern (B) semantic assurance pattern (C) systematic analysis pattern (D) systematic available pattern
KEY: 1-A, 2-C, 3-B, 4-D, 5-B, 6-B, 7-A, 8-C, 9-B, 10-A, 11-D, 12-C, 13-B, 14-A
Lecture Notes: Unit-4: Design Concepts, Architectural Design, Component-level Design
- why is design so important? => Answer is a single word—quality.
- interface design => software communicates with systems(interoperation) and humans (who use it).
- The architectural design => major structural elements of s/w, the architectural styles, design patterns, constraints
- The data/class => transforms class models to design class realizations (the imp data structures to implement the s/w)
- The component-level design = structural elements of the software architecture procedural description of software components.
- Functionality is assessed by evaluating the feature set, capabilities, generality and security of the overall system.
- Usability is assessed by considering human factors, overall aesthetics, consistency, and documentation.
- Reliability is evaluated by measuring the frequency and severity of failure, the accuracy of output results, the mean-time-to-failure (MTTF), the ability to recover from failure, and the predictability of the program.
- Performance is measured by considering processing speed, response time, resource consumption, throughput, and efficiency.
- Supportability combines the ability to extend the program (extensibility), adaptability, serviceability—these three attributes represent a more common term, maintainability—and in addition, testability, compatibility, configurability, the ease with which a system can be installed, and the ease with which problems can be localized.
 |
| Data-Centered Architecture |
 |
| Data-Flow Architecture |
 |
| Main Program / Sub-Program Architecture |
 |
| Layered Architecture |
 |
| Architectural Context Diagram |
 |
| Architectural Context diagram of SafeHome security function |
 |
| Components shown in above Figure are elaborated in this figure |
 | |
|
Assignment Unit-4
- Explain in detail Design Process.
- Demonstrate about Designing Class-Based Components
- Clearly explain about Architectural Mapping Using Data Flow
- Discuss in detail The Design Model
- Explain in detail Component-Level Design for WebApps
- Give a brief note on Design concepts
- Explain in detail Architectural Styles
- Explain in detail Component-Based Development.
- Explain how to Design Traditional Components.
Quiz Unit-4
1. A ___________ is a modular building block for computer software
(A) component (B) process (C) program (D) activity
2.A data abstraction is a named collection of data that describes a data object
(A) lesser (B) zero (C) higher (D) unpredictable
3. Software _________ alludes to “the overall structure of the software and the ways in which that structure provides conceptual integrity for a system.
(A) engineering (B) architecture (C) code (D) process
4. A ________ is a named nugget of insight which conveys the essence of a proven solution to a recurring problem within a certain context amidst competing concern.
(A) action (B) component (C) process (D) pattern
5. A ________ is a feature or behavior that is specified as part of the requirements model for the software
(A) drivers (B) concern (C) OS D) process.
6. __________ is the most common manifestation of separation of concerns
(A) concernity (B) Modularity (C) architecture (D) coding
7. __________ is a reorganization technique that simplifies the design (or code) of a component without changing its function or behavior
(A) refactoring (B) stories (C) process (D) coding
8. ______ implies a specific category within the overall software domain.
(A) Project (B) Plan (C) Genre (D) Coding
9. ________________ also called structured English or pseudocode, incorporates the logical structure of a programming language with the free-form expressive ability of a natural language (e.g., English)
(A) SEI (B) PDL (C) CMMI (D) ISO
10.__________ wrapping examines the internal processing details of the component and makes code-level modifications to remove any conflict.
(A) White-box (B) Blue box (C) Black-box (D) Gray-box
11.________ wrapping is applied when the component library provides a component extension language or API that enables conflicts to be removed or masked.
(A) White-box (B) Blue box (C) Black-box (D) Gray-box
12.________ wrapping requires the introduction of pre- and postprocessing at the component interface to remove or mask conflicts.
(A) White-box (B) Blue box (C) Black-box (D) Gray-box
KEY: 1-A, 2-C, 3-B, 4-D, 5-B, 6-B, 7-A, 8-C, 9-B, 10-A, 11-D, 12-C
Program design language (PDL)
Unit-5: UI Design, Software Quality Assurance, Testing (Strategies, Conventional Apps)
|
Place the user
in control |
Reduce the
user’s memory load |
Make the
interface consistent |
|
Do not force unnecessary actions Flexible interaction Interaction must be interruptible Customization Skill levels from basic to advance Hide technical internals from casual
user Direct interaction of objects that
appear on screen |
Reduce demand on short-term memory meaningful defaults Define shortcuts for intuitive Visual interface to be on a real-world
effect Disclose information in a progressive
fashion. |
Current task into a meaningful context Maintain consistency across a family of
applications. Past interactive model met user
expectations? If yes, then do not modify unless compiled. |
5.2 User Interface Analysis and Design
|
Models |
Types of users |
Process |
|
Human engineer creates user model s/w engineer creates Design model End user develops mental image model Implementers of the system create the Implementation
model. |
Novice: No idea/ No knowledge of the
system Intermittent users: reasonable syntactic
knowledge, but low recall Good syntactic knowledge , shortcuts. |
Spiral model: Focus on profile of users Define set of interface objects and
actions Prototype creating usage scenarios Interface Validation: User task implementation correctly Degree to which interface is easy to use
User’s acceptance level |
Assignment Unit-5
- Explain in detail User Interface Analysis and Design
- Demonstrate about Test Strategies for WebApps.
- Give a brief note on The Art of Debugging
- Discuss in detail Elements of Software Quality Assurance
- Explain in detail White-Box Testing, Basis Path Testing.
- Clearly explain about Validation Testing
- Explain in detail Test Strategies for Conventional Software.
- Explain in detail Software Testing Fundamentals
- Give a brief note on Software Quality Assurance Tasks.
Quiz Unit-5
1. These _________ actually form the basis for a set of user interface design principles that guide this important aspect of software design
(A) golden rules (B) agility (C) framework (D) task
2.A human engineer (or the software engineer) establishes a _______ model.
(A) implementation (B) component (C) user (D) unpredictable
3. When a number of different users, each playing different roles, makes use of a user interface, it is sometimes necessary to go beyond task analysis and object elaboration and apply ___________ analysis
(A) use cases (B) object elaboration (C) task elaboration (D) workflow
4. The use of navigation controls, menus, icons, and aesthetics (e.g., color, shape, layout) should be __________ throughout the WebApp
(A) bold or capital or italic (B) no protocol (C) different (D) consistent
5. The time to acquire a target is a function of the distance to and size of the target is called __________
(A) focus (B) Fitt's Law (C) flexibility D) efficiency
6. SQA = _________
(A) System Quantity Avoider (B) Software Quality Assurance (C) System Quality Assurance (D) Software Quality Analyzer
7. Core Steps of SixSigma are _____, ______, _______
(A) Define, Measure, Analyze (B) Design, Measure, Analyze (C) Design, Meetings, Analyze (D) Define, Measure, Apply
8. __________ refers to a different set of tasks that ensure that the software that has been built is traceable to customer requirements
(A) Verification (B) Validation (C) Variableness (D) Violation
9. _________ testing is actually a series of different tests whose primary purpose is to fully exercise the computer-based system
(A) Black Box (B) White Box (C) System (D) Unit
10. _________ occurs as a consequence of successful testing.
(A) Input (B) Debugging (C) Design (D) Architecture
KEY: 1-A, 2-C, 3-D, 4-D, 5-B, 6-B, 7-A, 8-B, 9-C, 10-B

.png)
.png)
.png)